
AI operates within defined scopes. Off-policy requests trigger alerts and are escalated or blocked.
Input is grounded & sanitized before reaching the model. Layered safeguards & supervision prevent injection.

Continuous learning require approval. Every decision and recommendation is audited.
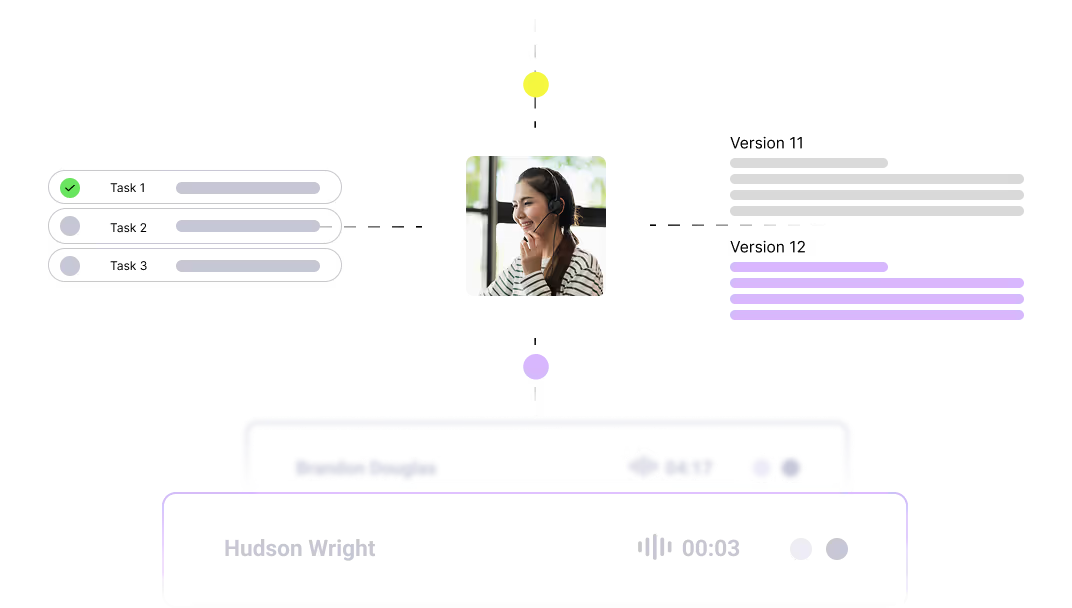
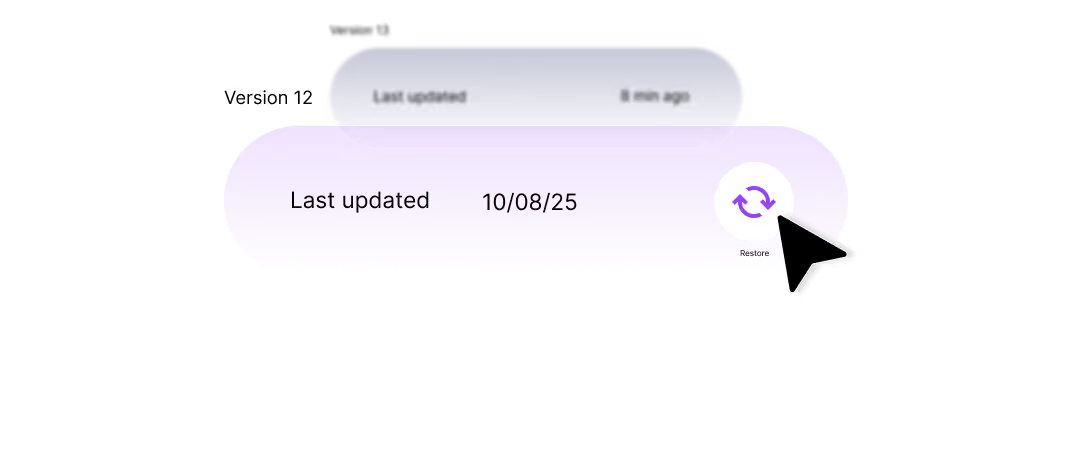
Versioned with one-click rollback. Continuous evaluations prevent regressions.
Inference-only, never shared across customers, retention/export/delete is fully configurable.
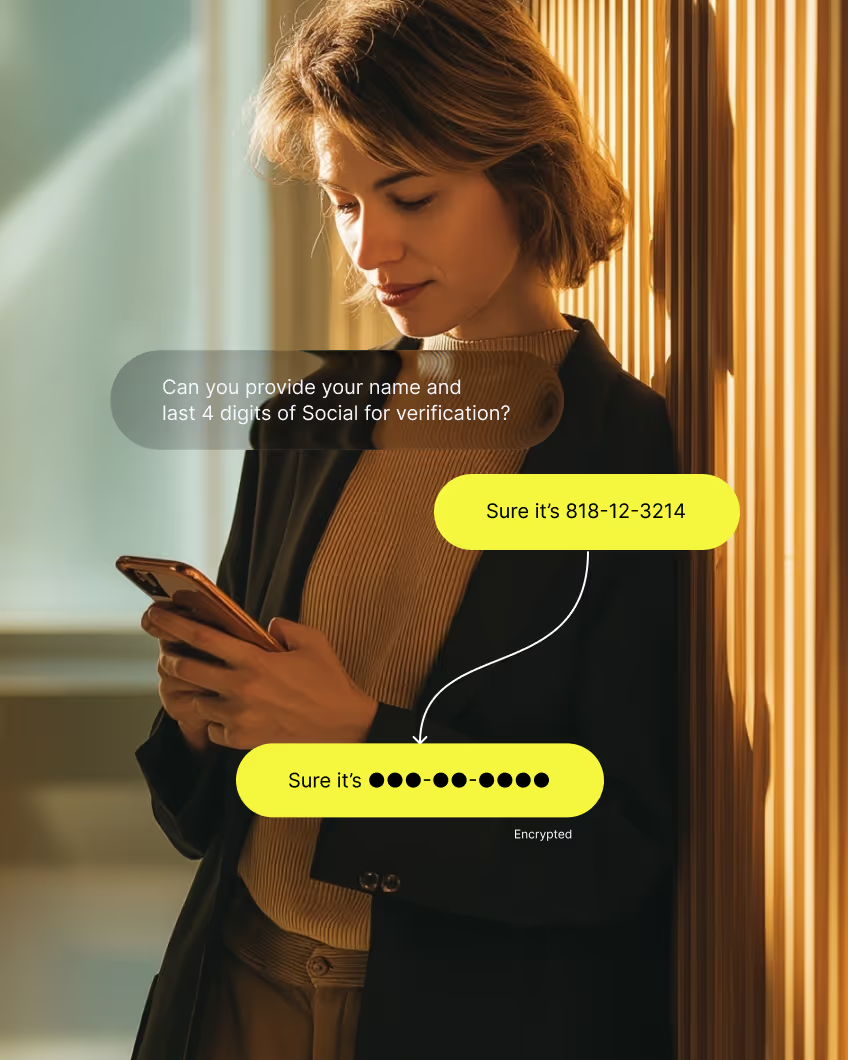
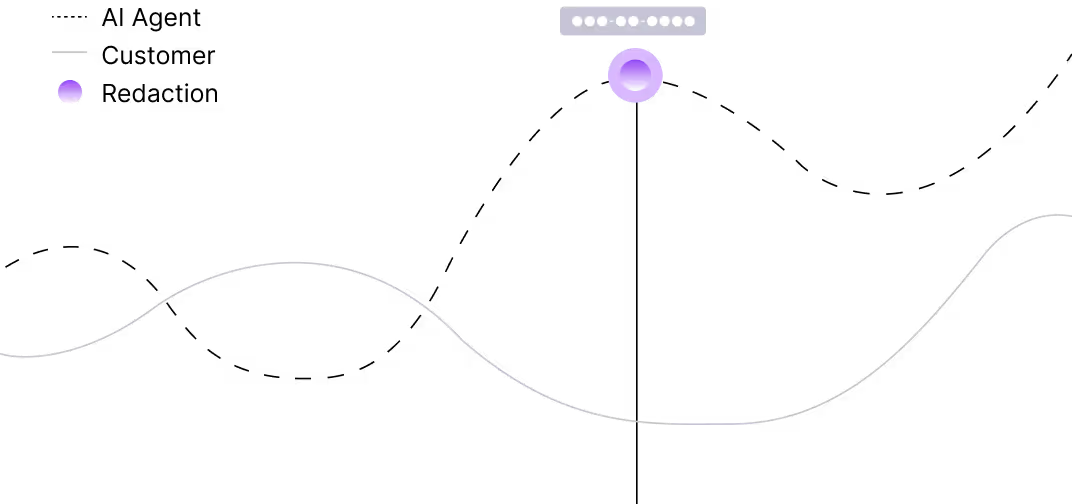
Encrypt in transit and at rest, pre-model redaction of PII/PCI/PHI, SSO/MFA, granular RBAC, BYOK/KYOK.
From pipeline to production, our software development life cycle (SDLC) includes end-to-end security controls: security project reviews, code reviews, vulnerability and penetration testing, and threat modeling/monitoring.

≥ 99.9% uptime

Global telemetry and alerting

Client due diligence, Compliance, Client pen tests

Fail Secure and policy guardrails
Your one stop for attestations, reports, sub-processors, security contacts, and FAQs.

Deploy AI with security, privacy, and governance built in.